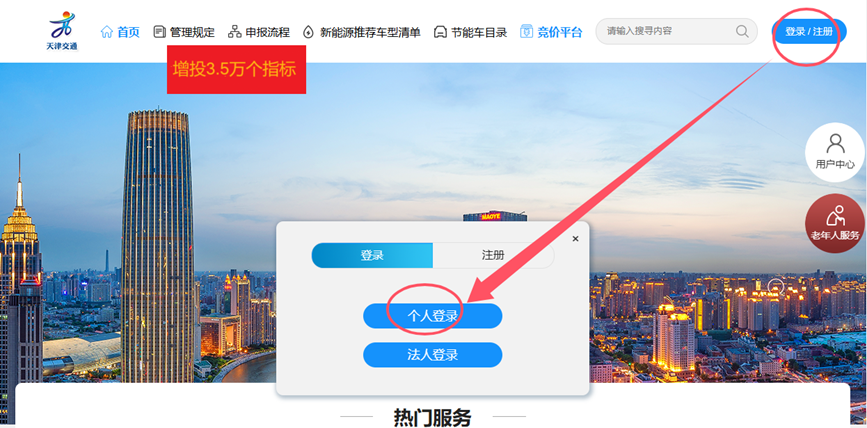
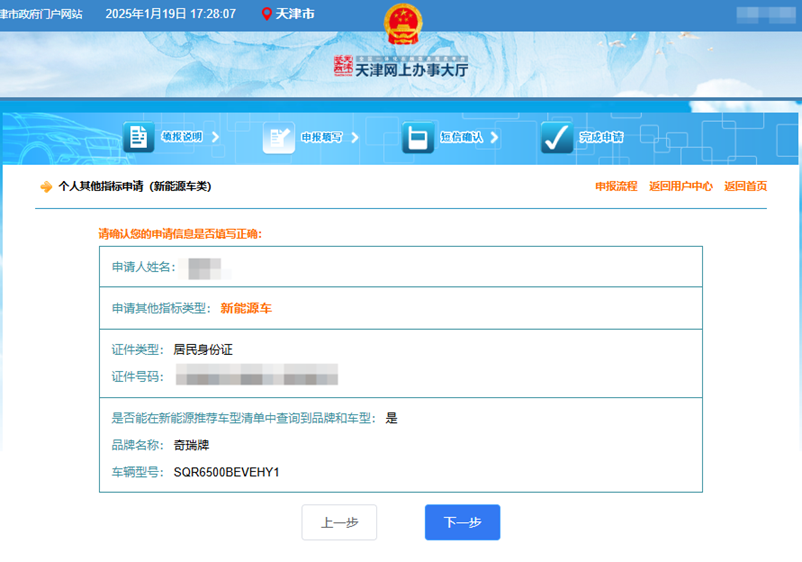
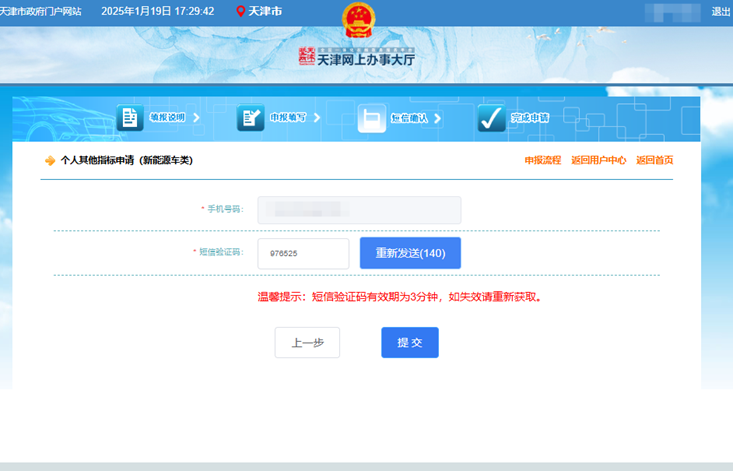
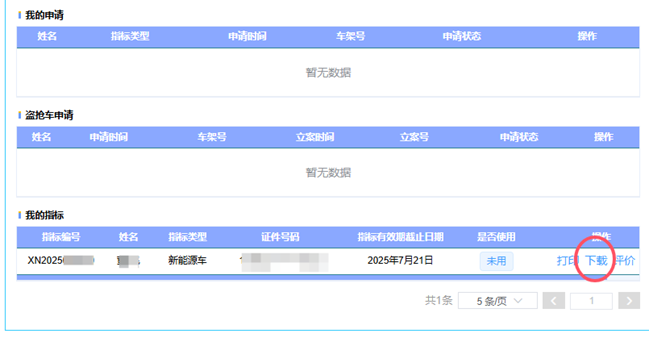
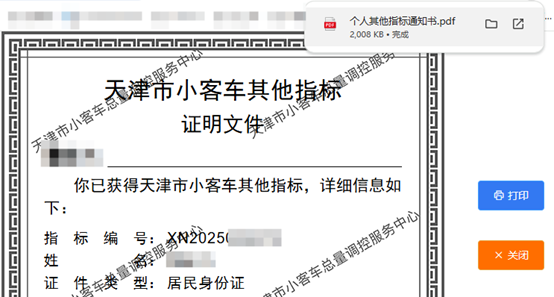
See PEP 668 for the detailed specification.
python安装组件报错。
其实很常见的了。要么用虚拟环境。要么就用系统包。
报错信息里面说的也比较明白。
典型报错信息如下:
pip3 install beautifulsoup4
error: externally-managed-environment
× This environment is externally managed
╰─> To install Python packages system-wide, try apt install
python3-xyz, where xyz is the package you are trying to
install.
If you wish to install a non-Debian-packaged Python package,
create a virtual environment using python3 -m venv path/to/venv.
Then use path/to/venv/bin/python and path/to/venv/bin/pip. Make
sure you have python3-full installed.
If you wish to install a non-Debian packaged Python application,
it may be easiest to use pipx install xyz, which will manage a
virtual environment for you. Make sure you have pipx installed.
See /usr/share/doc/python3.11/README.venv for more information.
note: If you believe this is a mistake, please contact your Python installation or OS distribution provider. You can override this, at the risk of breaking your Python installation or OS, by passing --break-system-packages.
hint: See PEP 668 for the detailed specification.重点可以看这部分:
╰─> To install Python packages system-wide, try apt install
python3-xyz, where xyz is the package you are trying to
install.PEP 668 引入的限制 —— 当前系统(比如 Debian 12 / Ubuntu 22.04+)为了保护系统自带的 Python,不允许你直接使用 pip 在系统环境中安装第三方包。.
推荐做法(不破坏系统环境):
用 apt 安装 BeautifulSoup(推荐,简单且安全)
apt update
apt install python3-bs4 -y这个包名是 python3-bs4,系统包管理器会帮你自动安装好依赖,不用 pip。
然后你可以直接在 Python 脚本中使用:
from bs4 import BeautifulSoup